Renovate vs Snyk: Automated Dependency Updates for Your Workflow
In software development, dependencies are external libraries, frameworks, or modules that a project relies on to function correctly. These can range from utility libraries to full-fledged frameworks that provide critical functionality. Managing these dependencies effectively is crucial for maintaining software stability, security, and performance. Projects can suffer compatibility issues, security vulnerabilities, and maintenance challenges when dependencies are not managed properly.
Here's where things get tricky. Dependencies can become outdated over time, introducing security vulnerabilities or compatibility issues. Keeping them updated manually is a constant tightrope walk. It's time-consuming, prone to errors, and can quickly derail your development flow.
Let's say you're using a popular image-processing library. An update might introduce a new, more efficient function. Great news, right? But what if this update breaks compatibility with another dependency in your project? Suddenly, you're facing a tangled mess of errors and delays.
This is why effective dependency management is crucial. By automating updates and ensuring compatibility, you can focus on building your application, not fixing its foundation.
Overview of Renovate
Renovate has become a popular choice for developers seeking an open-source solution. Renovate was created to address the growing challenge of managing dependencies in increasingly complex software environments. The primary purpose of Renovate is to ensure that dependencies are always up-to-date, thus reducing the risk of security vulnerabilities and improving overall software stability and performance.
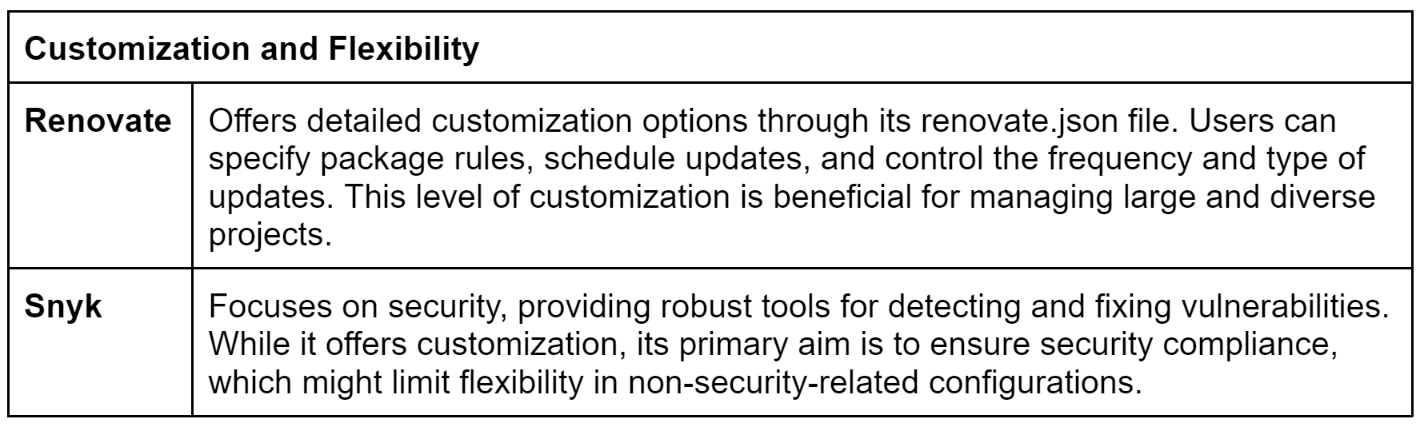
Key Features and Benefits
Renovate offers a robust set of features that make it a powerful tool for dependency management. Key features include:
-
Automated Dependency Updates: Renovate automatically scans for outdated dependencies and generates pull requests to update them. This reduces the manual effort required to maintain up-to-date dependencies.
-
Customizable Configuration: Using a renovate.json file, users can configure Renovate to meet their specific needs. This includes setting update schedules, grouping dependencies, and specifying automerge rules.
Our Amazing SponsorsDigitalOcean offers a simple and reliable cloud hosting solution that enables developers to get their website or application up and running quickly.View Website
Laravel News keeps you up to date with everything Laravel. Everything from framework news to new community packages, Laravel tutorials, and more.View Website
A Laravel Starter Kit that includes Authentication, User Dashboard, Edit Profile, and a set of UI Components. Learn more about the DevDojo sponsorship program and see your logo here to get your brand in front of thousands of developers.View Website
-
Enhanced Security: By keeping dependencies current, Renovate helps mitigate the risk of vulnerabilities associated with outdated libraries.
-
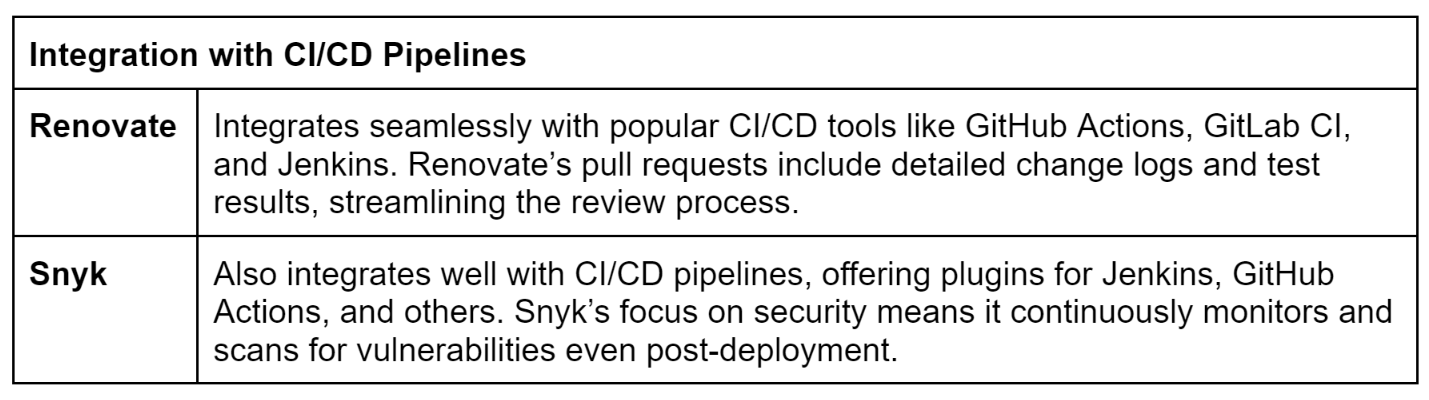
Integration with CI/CD Pipelines: Renovate integrates seamlessly with continuous integration and delivery pipelines, ensuring that updates are automatically tested and deployed.
Supported Environments and Integrations
Renovate supports a wide range of environments and integrations, making it versatile for different development workflows:
-
Version Control Systems: It is compatible with popular version control systems such as GitHub, GitLab, Bitbucket, and Azure Repos.
-
Package Managers: Renovate supports numerous package managers including npm, Yarn, Maven, Gradle, Docker, and many more. This extensive support ensures that it can be used across various types of projects and ecosystems.
How Renovate Works
Renovate functions by employing a configuration file, usually named renovate.json, which is situated in the root directory of the project. This file outlines the specific update management procedures for Renovate, such as the dependencies to be updated, the timing of updates, and the criteria for automating pull request merges. Key aspects of Renovate's workflow include:
-
Automated Pull Requests: When outdated dependencies are detected, Renovate creates pull requests with the necessary updates. These pull requests include detailed information about the changes and any potential impacts.
-
Customization Options: Renovate provides in-depth customization via package rules, enabling users to establish specific rules for various dependency types, implement update strategies, and consolidate dependencies to reduce the volume of pull requests.
-
Automerge Settings: To further streamline the update process, Renovate can be configured to automatically merge pull requests that meet predefined criteria, such as passing all CI checks and being limited to minor or patch updates.
By leveraging these features, Renovate simplifies the process of keeping dependencies up-to-date, enhancing both security and efficiency in software development projects.
Overview of Snyk
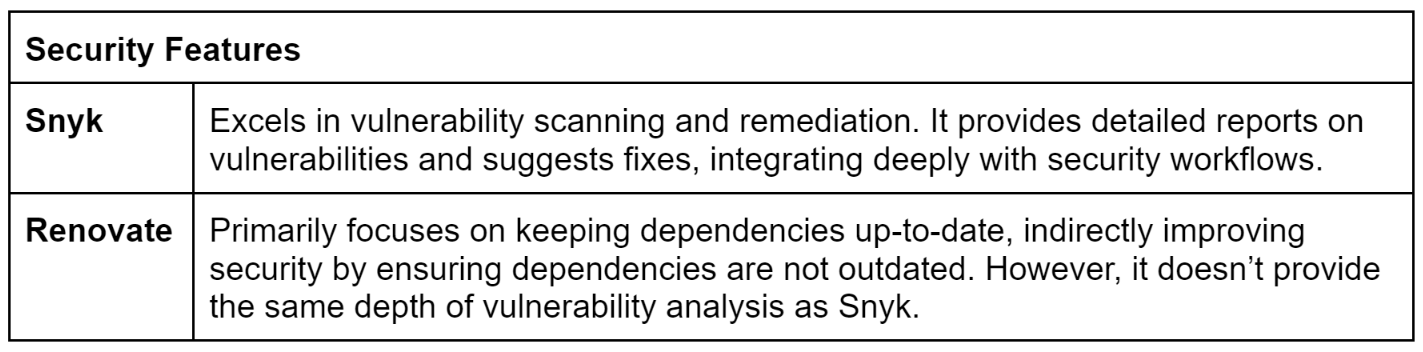
Snyk is a security platform designed for developers, focusing on identifying and addressing vulnerabilities in dependencies. Its primary goal is to integrate security measures into the development process, allowing developers to manage security concerns without disrupting their workflow. Snyk provides practical security insights and automates vulnerability resolution to enhance the overall security posture of software projects.
Snyk has established itself as a prominent player in software composition analysis (SCA) by continuously scanning dependencies for known security vulnerabilities, not just basic updates. When it detects a critical flaw, Snyk not only suggests an update but also guides remediation. This empowers developers to promptly and effectively patch vulnerabilities, reducing security risks.
Understanding that security should be seamlessly integrated, Snyk interfaces with popular CI/CD pipelines and development environments, allowing security checks to be incorporated into existing workflows. This ensures early identification and proactive resolution of vulnerabilities before they become production issues.
Key Features and Benefits
Snyk offers several features that set it apart as a comprehensive security tool:
-
Vulnerability Detection: Snyk scans for known vulnerabilities in dependencies and provides detailed information on the severity and potential impact of these issues.
-
Automated Fixes: The platform not only identifies vulnerabilities but also suggests and sometimes automatically applies patches or updates to fix these issues.
-
Continuous Monitoring: Snyk continuously monitors projects for new vulnerabilities and alerts users when new issues are discovered.
-
Developer-Friendly Integration: With seamless integration into the development workflow, Snyk ensures that security checks do not slow down development processes.
Security Focus
Snyk places a strong emphasis on security, particularly on detecting and remediating vulnerabilities. The tool integrates with security workflows to ensure that vulnerabilities are identified early in the development process and addressed promptly:
-
Vulnerability Detection: Snyk's robust database of known vulnerabilities helps in identifying security issues in dependencies, enabling developers to mitigate risks proactively.
-
Remediation: Snyk provides actionable remediation advice, including patches, version updates, and other fixes. It can automatically generate pull requests to apply these fixes, streamlining the process of securing the codebase.
-
Security Integration: Snyk integrates with existing security workflows and tools, enhancing the overall security posture of development projects.
Supported Environments and Integrations
Snyk is designed to work seamlessly with a variety of CI/CD pipelines and development environments, making it a versatile tool for different workflows:
-
CI/CD Pipelines: Snyk integrates with Jenkins, GitHub Actions, GitLab CI, CircleCI, and other popular CI/CD tools, ensuring security checks are part of the continuous integration process.
-
Development Environments: It supports integration with various development environments, including IDEs like Visual Studio Code and JetBrains, providing developers with real-time security feedback as they code.
-
Package Managers: Snyk supports a wide range of package managers such as npm, Maven, PyPI, and more, allowing it to scan and monitor dependencies across different ecosystems.
How Snyk Works
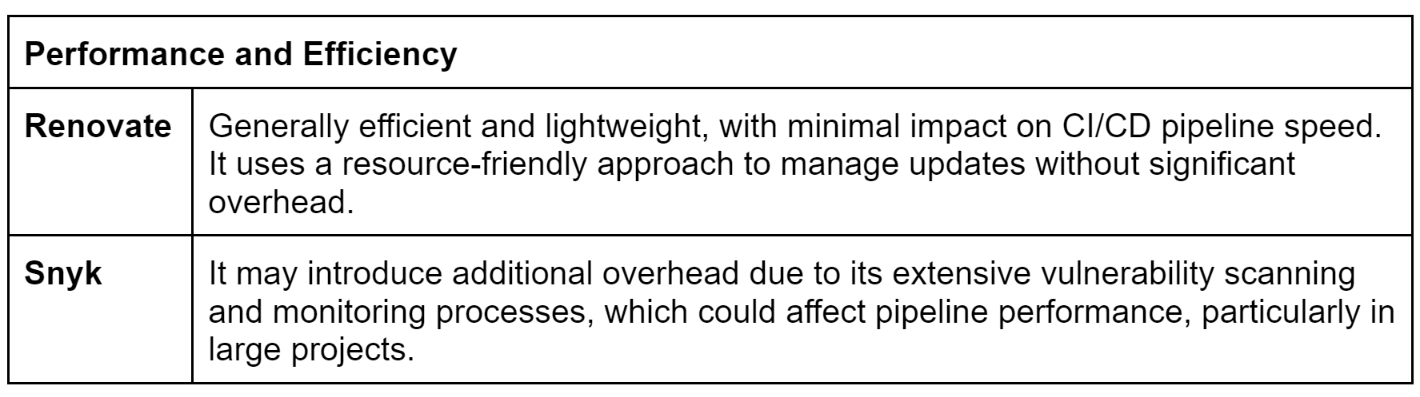
Snyk's behind-the-scenes leverages advanced technologies to analyze code. It can parse code structures, utilize solvers to identify vulnerabilities, and even employ machine learning algorithms to enhance its detection capabilities. This allows Snyk to efficiently scan large codebases and identify potential security risks.
Snyk operates through a combination of its CLI and a web-based dashboard, providing flexibility in how it can be used within different workflows:
-
Configuration: Users can configure Snyk through its CLI for integration into automated workflows or use the web dashboard for a more visual management approach.
-
Automated Pull Requests: Snyk automatically generates pull requests for identified vulnerabilities and dependency updates, providing suggested fixes and details on the issues being addressed.
-
CI/CD Automation: With integration into CI/CD tools like Jenkins and GitHub Actions, Snyk can automate the merging of security fixes and dependency updates, ensuring that these improvements are consistently applied without manual intervention.
By focusing on integrating security into the development lifecycle, Snyk helps teams maintain secure, up-to-date codebases efficiently, significantly reducing the risk of vulnerabilities in production environments.
Comparative Analysis
Comparing Renovate and Snyk is crucial for selecting the right tool tailored to your specific needs in managing dependencies. Both tools offer unique features that enhance dependency management and security, but understanding their differences can help optimize your development workflow.
Let's compare them across key factors to help you choose the perfect tool for your project.

In summary, we can compile the comparison above into the features table below, showing each tool's strengths and weaknesses.
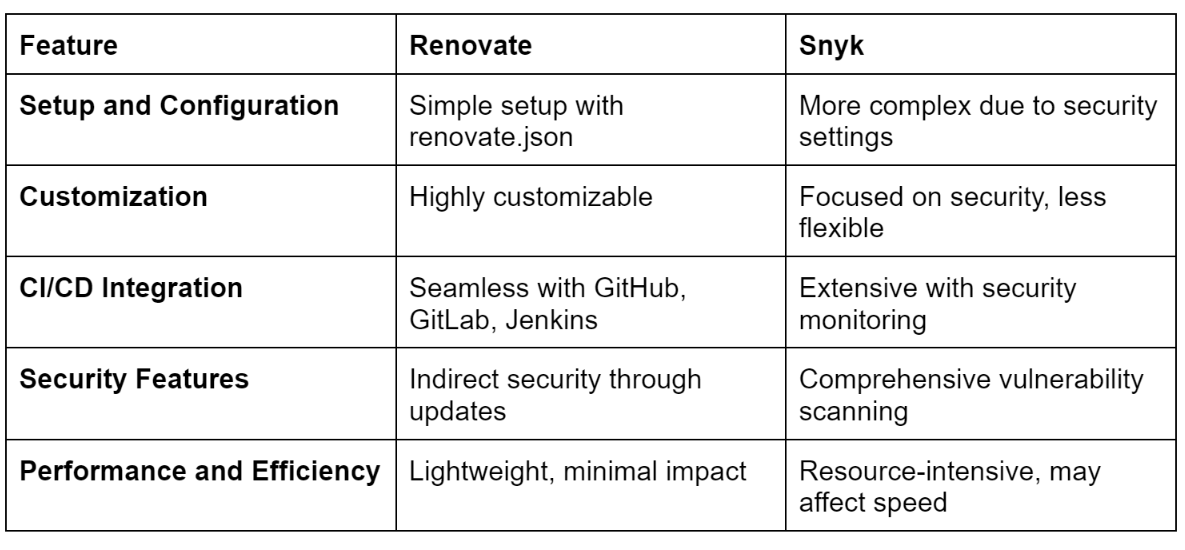
Practical Choice Based on Project Size and Complexity
For small to medium-sized projects, choosing between Renovate and Snyk largely depends on the project's needs and complexity. Renovate is ideal for projects primarily concerned with keeping dependencies up-to-date without significant security overhead. Its simple setup and configuration make it easy to integrate into smaller projects, allowing developers to focus on feature development while ensuring dependencies are current.
Snyk, on the other hand, offers comprehensive security features, making it suitable for projects that require robust vulnerability management alongside dependency updates. While the setup may be slightly more complex, the added security benefits can be crucial for projects handling sensitive data or operating in regulated industries.
Example Scenarios and Configurations
- Renovate: A small e-commerce website using Node.js and npm can configure Renovate with a basic renovate.json file to handle updates automatically. The configuration might include rules to update minor and patch versions, reducing the need for manual intervention:
{\
"extends": ["config:base"],\
"packageRules": [\
{\
"updateTypes": ["minor", "patch"],\
"automerge": true\
}\
]\
}
- Snyk: A medium-sized SaaS application using Java and Maven can leverage Snyk's CLI to integrate vulnerability scanning into its CI/CD pipeline. The setup includes automated pull requests for security fixes and continuous monitoring for new vulnerabilities:
Steps:
- name: Snyk Security Scan\
run: snyk test --all-projects\
- name: Snyk Monitor\
run: snyk monitor --all-projects
Enterprise projects often entail intricate dependency hierarchies and strict security standards. Renovate can be customized to manage large-scale updates by categorizing dependencies and scheduling updates during non-peak hours to minimize disruptions. Its automerge capability reduces manual work, allowing teams to concentrate on more critical tasks.
For enterprises, Snyk's comprehensive security features are invaluable. Snyk provides detailed vulnerability reports, compliance checks, and integration with enterprise security workflows. This ensures that all dependencies adhere to corporate security standards and regulatory requirements, making it the preferred choice for enterprise environments.
Best Practices
Ensuring proper dependency management is crucial for upholding the stability, security, and efficiency of a software project. By adhering to best practices in this area, you can maintain a healthy codebase, minimize the risk of introducing vulnerabilities, and streamline the development process.
Configuration Management
- Use Presets and Extends: Leverage existing presets and extensions to reduce redundancy. For instance, Renovate's extends feature allows you to inherit configurations from shared presets, ensuring consistency and simplicity in your configuration files.
{\
"extends": ["config:base"]\
}
-
Modular Configuration: Break down large configurations into smaller, manageable pieces. This can be done by using modular configuration files that are combined as needed.
-
Clear Documentation: Document each configuration setting within the file. Adding comments helps in understanding the purpose of each setting and facilitates easier maintenance.
{\
"extends": ["config:base"],\
// Automerge minor updates\
"packageRules": [\
{\
"updateTypes": ["minor"],\
"automerge": true\
}\
]\
}
- Validation Tools: Utilize tools that validate your configuration files to catch errors early. This ensures that the configurations are syntactically correct and will function as expected.
Security and Compliance
- Security Scans: Regularly scan for vulnerabilities using tools like Snyk. Integrate these scans into your CI/CD pipeline to catch issues before they reach production.
Steps:
- name: Snyk Security Scan\
run: snyk test --all-projects
-
Dependency Pinning: Pin dependencies to specific versions to avoid unintentional updates that might introduce vulnerabilities. This practice ensures a predictable and stable dependency graph.
-
Review and Approve Updates: Implement a review process where dependency updates are reviewed and approved by senior developers or security experts. This adds an additional layer of scrutiny to the update process.
-
Continuous Monitoring: Use tools that continuously monitor dependencies for new vulnerabilities. Snyk provides continuous monitoring and alerting for new vulnerabilities in existing dependencies.
-
Regular Audits: Conduct regular security audits to assess the overall security posture of your dependencies. These audits should be scheduled and documented as part of your security policies.
Continuous Improvement
- Automated Updates: Use automation tools like Renovate to keep dependencies up to date without manual intervention. Configure these tools to automatically merge safe updates to ensure dependencies are current.
{\
"extends": ["config:base"],\
"packageRules": [\
{\
"updateTypes": ["minor", "patch"],\
"automerge": true\
}\
]\
}
-
Tool Updates: Regularly update the dependency management and security tools themselves to leverage new features and improvements.
-
Feedback from Developers: Create a feedback loop where developers can report issues and suggest improvements for the dependency management process. This can help in fine-tuning configurations and practices.
-
Performance Monitoring: Monitor the performance impact of dependency updates and security scans on the CI/CD pipeline. Optimize configurations to balance security and efficiency.
By adhering to these best practices, teams can uphold streamlined and effective configurations, guarantee strong security and compliance, and perpetually enhance their dependency management processes, ultimately boosting the stability and security of their software projects.
Conclusion
When choosing between Renovate and Snyk, consider your specific project needs.
Use Renovate if your primary goal is to automate dependency updates efficiently and you require extensive customization options. Renovate is especially suitable for small to medium-sized projects and open-source initiatives where keeping dependencies up-to-date with minimal manual intervention is critical.
Opt for Snyk if security is a major concern. Its powerful vulnerability scanning and remediation capabilities make it a preferred choice for enterprise-level projects and applications handling sensitive data or operating under stringent regulatory requirements.
To ensure comprehensive software health and security, it is recommended to integrate Renovate for managing routine dependency updates and Snyk for continuous monitoring and fixing of vulnerabilities. This dual approach guarantees that dependencies remain up-to-date and secure, thereby strengthening the resilience and reliability of software projects.
Encouraging the integration of these tools in the development workflow not only streamlines dependency management but also reinforces software against potential security threats, resulting in a more robust and secure development lifecycle.

Comments (0)