Laravel Security
A zombie developer doesn't care about security, whereas a Laravel developer can rest assure that their app is secure from some of the most common app vulnerabilities.
We want to make sure that no one can hack into our application, and luckily Laravel has been built to prevent some of the most common ways that users hack into systems.
Security
Security is an important thing when it comes to building applications. Luckily for us, we have decided to use Laravel which includes security features such as SQL Injection, Cross Site Scripting, and Cross Site Request Forgery.
Don't worry if you don't know much about any of these protections. We'll explain them below:
SQL Injection
SQL Injection is when someone tries to hack an input that gets submitted into the database. Say we were to run a SQL command like so:
$weapon_name = $_POST['weapon_name'];
$query = 'INSERT INTO weapons VALUES ('1', $weapon_name);
The user could easily enter in a value to the weapon name to Inject SQL into our query. So, they could potentially run a query and drop a table or a database.
Check out this XKCD.com comic:
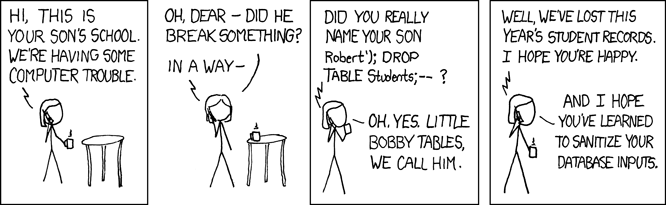
Thanks to Laravel and Eloquent we don't have to worry about SQL injection.
Cross Site Scripting
Cross-site scripting occurs when a hacker adds malicious code in the form of a client side script. So, pretend you have a comment text area and someone put in the following and submitted it as a comment:
<script>alert('hello, I just hacked this page');</script>
Now whenever someone visits that page, they will be alerted with this annoying popup. You can see that this could be dangerous because the user could even redirect that page to another page.
Thankfully by using the blade templating engine we can output any data and protect against Cross-site Scripting attacks by using the triple curly brace syntax:
{{{ $user_comment }}}
That output above would be sanitized to prevent any Cross-site Scripting (also referred to as XSS attack).
Cross-site Request Forgery
Finally, there is another attack called Cross Site Request Forgery that Laravel can prevent against. This occurs someone modifies a POST/PUT/DELETE request being sent to your server.
A possible scenario is a hacker who modifies the data being sent by a request from the browser to the server. The hacker could intercept the request and swap out values, causing the web application to perform functionality that it normally might not have.
Thankfully, Laravel is here to save the day against CSRF attacks.
When you submit a form you can include a hidden input type with a name of _token and the value of csrf_token() and Laravel will handle the rest. The form will look similar to the following:
<form method="POST" action="/zombie">
...
<input type="hidden" name="_token" value="{{ csrf_token() }}">
<input type="submit">
</form>
And Laravel will handle all the rest. If a POST/PUT/DELETE request is submitted and the security token does not match, the data will not be posted to the application, which will prevent a hacker from intercepting the request.
So, now you can sleep peacefully knowing that your site is safe against any CSRF attacks.
Working on security issues can be time consuming, but thanks to Laravel we can focus on what we enjoy most, which is building our app.